:quality(80)/business-review.eu/wp-content/uploads/2020/04/dreamstime_s_116177450.jpg)
As the number of cyber-crimes has been seeing a dramatic increase in recent weeks, hackers taking advantage of the Coronavirus pandemic to lure unsuspecting victims, Romanian cyber-security company Safetech Innovations decided to release a step-by-step guide on how to detect fraudulent e-mails and avoid becoming the victim of a phishing attack (info-graphic included at the end of this article).
Phishing attacks are used very often by hackers, either to obtain personal data or to spread malware. In general, phishing attacks include sending emails that seem to come from known acquaintances, or from trusted institutions. The topics of these types of emails generally raise the recipient’s interest and invite him or her to open the email, read it, click on the attachment or a link and even fill in a personal data in a specially developed form.
The current context of COVID-19 outbreak has been used by the hackers in order to spread phishing attacks as a significant number of attempts has been recorded in March 2020. Researchers at Barracuda Networks, who provide network security to 220,000 global corporate customers, reported that the volume of coronavirus-related email attacks spiked by 667% since February 2020, reaching more than 9,000 incidents in March alone. More specifically, between 1st and 23rd of March, Barracuda detected 467,825 spear-phishing email attacks around the world, and 9,116 of those were related to COVID-19.
On April 6th, the Romanian Police has announced on its Facebook page that there has been a phishing attempt where hackers are sending fraudulent emails on behalf of the police, warning the citizens not to open the attachment to the email.
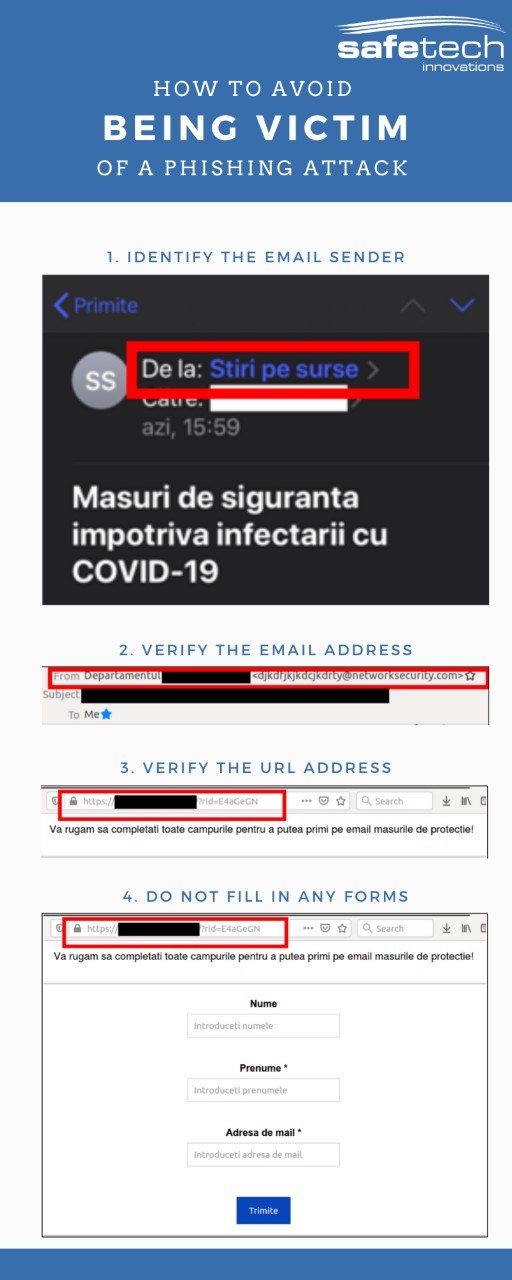
Despite the significant increase, the phishing attacks via email are relatively easy to be spotted if the user is paying attention. In order to avoid being the victim of a phishing attack, the Internet users should follow the following simple steps:
- Identification of the sender. On a mobile phone, the information is truncated, generally only a part of the sender’s address, or its associated description is visible. Therefore, it is recommended that suspicious messages be opened on a desktop or laptop, where more information can be obtained. If already at this moment we spot that the message is not something we have ever subscribed to and it also looks like spam, it is recommended to delete the message.
- Verifying the email address from which the message was sent. One thing that can draw attention is that often such email addresses have randomly generated names. Also, the urgency with which a form is required, as well as the information promised after filling it, can attract suspicion.
- Verification of URL. If you go further and press the button in the email, you can reach generally reach a web form, where your personal data is requested. Particular attention should be paid to the URL in the browser, which may provide additional information about the entity collecting the data.
- Do not fill in any form without verifying authenticity of the website. Once the fields in the online form are completed, the information provided is collected and can be used for various purposes. For example, the password entered by a person in the registration form can also be then used on different personal accounts, with hacker trying to access different accounts with the same password or variations of it. Often information collected in such manner is sold on the market on the so-called “dark web”.
In the context of COVID-19 pandemic, some online websites which are giving at the disposal the web forms to fill in the Declarația pe propria răspundere, necessary for any movement, can also be phishing attempts. In this case, the malicious URL reaches potential victims not the email, but through the social networks. The data collected by the respective websites can be used for various purposes, such as performing hacking activities on behalf of the person who completed the form, or identifying the time intervals when a person is not in his / her home, in order to organize a theft at that address. In this particular case, it is recommended to only use the declaration from the websites of state institutions, a statement that can be downloaded, printed and filled in manually, without the personal information being transmitted over the Internet.




:quality(80)/business-review.eu/wp-content/uploads/2024/04/Simona-Moisa-Dentons.jpg)




:quality(80)/business-review.eu/wp-content/uploads/2024/02/IMG_6951.jpg)

:quality(80)/business-review.eu/wp-content/uploads/2024/04/COVER-1.jpg)



:quality(50)/business-review.eu/wp-content/uploads/2018/07/gdpr.jpg)
:quality(80)/business-review.eu/wp-content/uploads/2024/04/cover-april.jpg)
:quality(50)/business-review.eu/wp-content/uploads/2024/04/FOT_9989-7-scaled.jpg)
:quality(50)/business-review.eu/wp-content/uploads/2023/08/One-Floreasca-City-2-scaled.jpg)
:quality(50)/business-review.eu/wp-content/uploads/2024/04/ROMTEXTIL-2.jpg)