Do you remember the WannaCry ransomware attack, which in May 2017 made thousands of victims in 150 countries, including Romania? One thing is for sure: in the ever-evolving threat landscape and rapidly growing network environments, no one remains safe. Today’s target cyber attacks are more sophisticated and threat actors are better at hiding and staying undetected within your business.
Whether the attackers are after financial data, trade secrets, or classified information, it is no longer a matter of if, but when, attackers will break into your network. They’ll use zero-day attacks, stolen access credentials, infected mobile devices, a vulnerable business partner, or other tactics.
Wonder if there’s a solution to keep threats out of your network or to quickly respond to an attack when it happens?
Cisco Stealthwatch serves as the eyes and ears of the network. Cisco Stealthwatch is the industry-leading security analytics solution providing comprehensive threat visibility into the extended network. It can detect and respond to advanced threats, and help simplify network segmentation using a combination of behavioral modeling, multilayered machine learning, and global threat intelligence. And it is the first and only solution in the industry that can detect malware in encrypted traffic without any decryption using Encrypted Traffic Analytics.
Troubleshooting reduced from days or even months to just minutes
When combined with other Cisco security technologies, Stealthwatch helps organizations cost-effectively use their existing infrastructure to turn their network into an always-on security sensor for more seamless threat detection. Through sophisticated behavioral analytics, Stealthwatch can automatically detect suspicious behaviors that could lead to a wide range of attacks, from zero-day malware and distributed denialof-service (DDoS) attacks to advanced persistent threats (APTs) and insider threats.
Also, Stealthwatch dramatically reduces the manual analysis associated with incident investigation. It often reduces troubleshooting down from days or even months to just minutes. Intuitive dashboards and reports help security and incident response professionals rapidly get to the information they need with just a few clicks, whether it’s an overall picture of network activity, a list of potential issues, or a view into a specific host (See Stealthwatch Dashboard below).
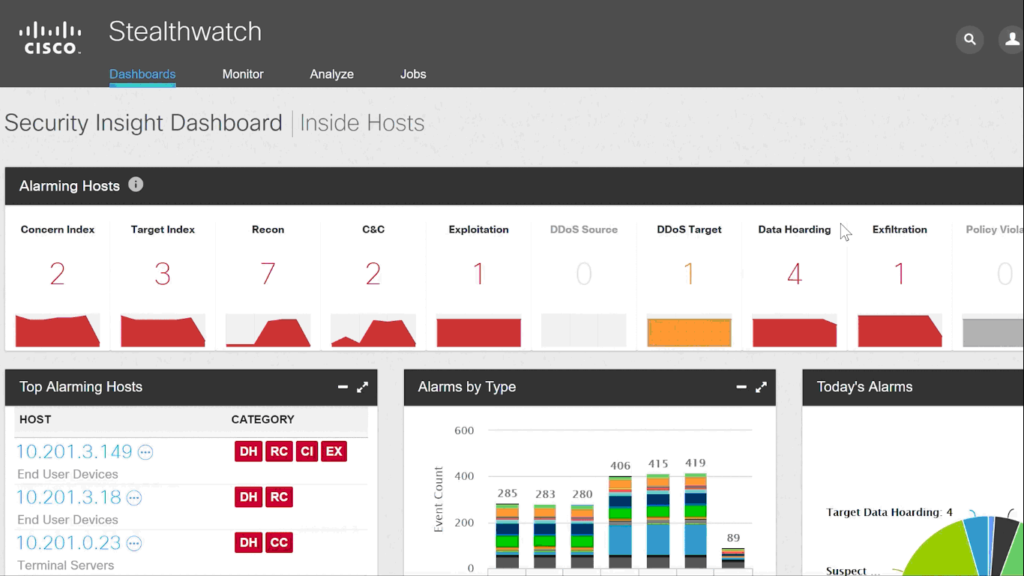
Perhaps an insider is repeatedly trying to access restricted areas of your network. Or maybe unusually large amounts of data are being sent out of your network, or an internal host is communicating with a suspicious IP address in a foreign country. An effective network visibility and security analytics tool can pick up on these behaviors and alert administrators to investigate further.
Unlike many other technologies that only monitor traffic going in and out of the network, Stealthwatch also monitors lateral (east-west) traffic to detect attacks spreading inside the network and identify insider threats. By constantly monitoring the network for anomalous behavior—and using advanced security analytics, alarming, and reporting to alert administrators to potential issues—Stealthwatch enables faster, more efficient incident response.
In addition to improving real-time threat detection, Stealthwatch also helps you conduct faster, more thorough investigations. It can store flow data for months or even years and use its advanced querying capabilities to quickly extract pertinent information about previous attacks. The ability to efficiently collect, analyze, and interpret huge volumes of network and security data will become even more important as networks continue to grow and evolve through cloud, software-defined networking (SDN), and Internet of Things (IoT) architectures.
Unfortunately, no technology today can completely keep hackers out of enterprise networks. However, if an organization is regularly monitoring its own environment with the right mix of people, processes, and technology, the security team will be better equipped to identify and stop an attack while it’s still happening, avoiding the disastrous results and costs associated with a data breach.
Combined with Cisco’s broad security portfolio, Stealthwatch can provide comprehensive protection and streamlined incident response across the network, data center, endpoints, mobile devices, and the cloud.


:quality(80)/business-review.eu/wp-content/uploads/2019/01/Security.jpg)

:quality(80)/business-review.eu/wp-content/uploads/2024/04/coffeeast-3.jpeg)




:quality(80)/business-review.eu/wp-content/uploads/2024/02/IMG_6951.jpg)

:quality(80)/business-review.eu/wp-content/uploads/2024/04/COVER-1.jpg)



:quality(50)/business-review.eu/wp-content/uploads/2023/09/Faruk-Hairedin-Business-Development-Director-Datanet-Systems.png)
:quality(80)/business-review.eu/wp-content/uploads/2024/04/cover-april.jpg)
:quality(50)/business-review.eu/wp-content/uploads/2024/04/Slide1.png)
:quality(50)/business-review.eu/wp-content/uploads/2024/04/1_Transport.jpg)
:quality(50)/business-review.eu/wp-content/uploads/2024/04/0x0-Supercharger_18-scaled.jpg)